Pentagram Secure Services
- Home
- Services

We're here to secure your business Technologies
IT infrastructure has changed dramatically in recent decades. We give the proper knowledge to protect your firm from being attacked by cyber bullies by identifying threats in your organization.
Black Box/ White Box /Wireless /Mobile (Android& iOS)/WebApp.
Computer /Accounting/ Expert Witnesses.
- Social Engineering Campaign.
- Firewall Rules Review.
- Office 365 /Azure Security Architecture Review.
- Security Operations Centre (SOC) 24X7.
- ICS/Scada Vulnerability Assessment.
- Smart City.
We Build Secure Systems
Our Cybersecurity Services

Black Box Pen-Testing
Using state-of-the-art software scanning tools and manual techniques, our external security assessment looks for areas that may be exposed to malicious attacks through your firewall or through social engineering.

White Box Pen-Testing
Evaluate the quality of your internal network technical control by performing a deep scan of all internal IP addresses. Our internal security also assessment prioritizes potential vulnerabilities.

Wireless Pen-Testing
Wireless penetration testing is a method of identifying and exploiting security weaknesses in Wi-Fi networks. It is an essential measure for organizations that depend on wireless networks for their operations.
IOS Pen-Testing
iOS Penetration Testing is the process of identifying and exploiting vulnerabilities in iOS applications. The method may include decompiling the application to identify any defects that could lead to bugs.

IT EXAM
A full evaluation of your information security and IT policies, procedures and controls will determine the adequacy of your security and risk management efforts. Our IT exam identifies areas where you’re most at risk and provides a detailed review of your environment to confirm compliance with industry regulations and guidelines. Recommended actions are provided as a road map to ensure your institution has a well-secured and compliant IT environment

White Box Pen-Testing
Evaluate the quality of your internal network technical control by performing a deep scan of all internal IP addresses. Our internal security also assessment prioritizes potential vulnerabilities.

Wireless Pen-Testing
Wireless penetration testing is a method of identifying and exploiting security weaknesses in Wi-Fi networks. It is an essential measure for organizations that depend on wireless networks for their operations.

IOS Pen-Testing
iOS Penetration Testing is the process of identifying and exploiting vulnerabilities in iOS applications. The method may include decompiling the application to identify any defects that could lead to bugs.

Black Box Pen-Testing
Using state-of-the-art software scanning tools and manual techniques, our external security assessment looks for areas that may be exposed to malicious attacks through your firewall or through social engineering.

Mobile or Android Pen-Testing
Mobile or Android penetration testing aims to detect security vulnerabilities and ensure that mobile applications are not vulnerable to attack.

Web Pen-Testing
Your website can be a portal for hackers to launch an attack on your network. Our web application assessment examines critical security issues in web applications and performs tests to identify threats and assess your website's overall risk.

Computer forensics
Identification, acquisition, processing, analysis and reporting of electronically stored data. Electronic evidence is a component of almost all criminal activity and computer forensic support is crucial to police investigations.

Forensic accounting
Forensic accounting uses accounting, auditing, and investigative skills to conduct an examination of the finances of an individual or business. Forensic accounting provides accounting analysis that can be used in legal proceedings.

Mobile or Android Pen-Testing
Mobile or Android penetration testing aims to detect security vulnerabilities and ensure that mobile applications are not vulnerable to attack.

Web Pen-Testing
Your website can be a portal for hackers to launch an attack on your network. Our web application assessment examines critical security issues in web applications and performs tests to identify threats and assess your website's overall risk.

Computer forensics
Identification, acquisition, processing, analysis and reporting of electronically stored data. Electronic evidence is a component of almost all criminal activity and computer forensic support is crucial to police investigations.

Forensic accounting
Forensic accounting uses accounting, auditing, and investigative skills to conduct an examination of the finances of an individual or business. Forensic accounting provides accounting analysis that can be used in legal proceedings.

Expert witnesses
To help the judge or jury understand electronic evidence, enabling them to make factual decisions on matters relating to electronically stored information involved in the case.

Social Engineering Assessment
As your employees gather information online and unwittingly download viruses and malware, your entire network could be compromised with the click of a button.We test your employees' responses to a simulated attack and provide feedback on leading practices to better secure your organization against social engineering threats.

Firewall rules review
A firewall configuration review involves performing a detailed manual review of your firewall configuration, looking for deviations from security best practices and potential security vulnerabilities.

Office 365 Azure Security Architecture Review
Perform a security best practices review of your Azure/O365 environments with prioritized recommendations for hardening.

Expert witnesses
To help the judge or jury understand electronic evidence, enabling them to make factual decisions on matters relating to electronically stored information involved in the case.

Social Engineering Assessment
As your employees gather information online and unwittingly download viruses and malware, your entire network could be compromised with the click of a button.We test your employees' responses to a simulated attack and provide feedback on leading practices to better secure your organization against social engineering threats.

Firewall rules review
A firewall configuration review involves performing a detailed manual review of your firewall configuration, looking for deviations from security best practices and potential security vulnerabilities.

Office 365 Azure Security Architecture Review
Perform a security best practices review of your Azure/O365 environments with prioritized recommendations for hardening.

Penetration test
A penetration test exploits vulnerabilities found in internal and external security assessments through proof-of-concept attacks. These tests help you better understand the extent to which an attacker can exploit vulnerabilities by destroying systems, denying service, stealing data, and taking other malicious actions.

SOC
Security Operations Center (SOC) works for you 24x7 - attackers never sleep and neither do we.We leverage Next-gen SIEM, AI, UBA and Threat Intel combined with a team of cybersecurity experts to protect your business 24x7 at a lower starting price than it would cost you to hire a single security analyst .

MONITORING AND TRIAGE SOC 24X7
¤ User Behavior Analysis (UBA). ¤ MITER ATT&CK Framework. ¤ Command and control and botnets. ¤ Malware/Ransomware. ¤ Phishing/spear phishing attacks. ¤ Indicators of compromise. ¤ Privileged access monitoring. ¤ Escalation of privileges. ¤ Lateral movement attacks. ¤ Movements impossible. ¤ Unauthorized access. ¤ Brute force attacks. ¤ VPN access anomalies. ¤ Policy violation and incorrect configurations. ¤ Suspicious activities. ¤ Defense escape. ¤ Data exfiltration. ¤ DoS/DDoS.

SUPPORTED LOG SOURCES
¤ Server infrastructure. ¤ Workstations/Laptops/Remote Work and Firewalls/IDS. ¤ Domain controllers. ¤ Email solutions. ¤ Web proxies. ¤ Antivirus/EDR. ¤ Cloud apps. ¤ Enterprise apps. ¤ Custom legacy apps. ¤ Routers/switches. ¤ DevOps.

Penetration test
A penetration test exploits vulnerabilities found in internal and external security assessments through proof-of-concept attacks. These tests help you better understand the extent to which an attacker can exploit vulnerabilities by destroying systems, denying service, stealing data, and taking other malicious actions.

SOC
Security Operations Center (SOC) works for you 24x7 - attackers never sleep and neither do we.We leverage Next-gen SIEM, AI, UBA and Threat Intel combined with a team of cybersecurity experts to protect your business 24x7 at a lower starting price than it would cost you to hire a single security analyst .

MONITORING AND TRIAGE SOC 24X7
¤ User Behavior Analysis (UBA). ¤ MITER ATT&CK Framework. ¤ Command and control and botnets. ¤ Malware/Ransomware. ¤ Phishing/spear phishing attacks. ¤ Indicators of compromise. ¤ Privileged access monitoring. ¤ Escalation of privileges. ¤ Lateral movement attacks. ¤ Movements impossible. ¤ Unauthorized access. ¤ Brute force attacks. ¤ VPN access anomalies. ¤ Policy violation and incorrect configurations. ¤ Suspicious activities. ¤ Defense escape. ¤ Data exfiltration. ¤ DoS/DDoS.

SUPPORTED LOG SOURCES
¤ Server infrastructure. ¤ Workstations/Laptops/Remote Work and Firewalls/IDS. ¤ Domain controllers. ¤ Email solutions. ¤ Web proxies. ¤ Antivirus/EDR. ¤ Cloud apps. ¤ Enterprise apps. ¤ Custom legacy apps. ¤ Routers/switches. ¤ DevOps.

WHAT SPSM/MSSPS AND END CUSTOMERS GET
¤ 24x7 detection, analysis and triage of threats in a multi-tenant environment. ¤ Custom reports without white label. ¤ Weekly/monthly SOC reports. ¤ Recurring SOC governance calls. ¤ Access to customer data. ¤ Over 750 custom security rules. ¤ Access to the SOC ticket management portal. ¤ Automation and incident response. ¤ Custom SOC Escalations. ¤ ALS GOLD of 30 minutes. ¤ Retention of logs from 90 days to 1 year. ¤ Assigned named SOC analysts. ¤ Local number dedicated to SOC 1800.
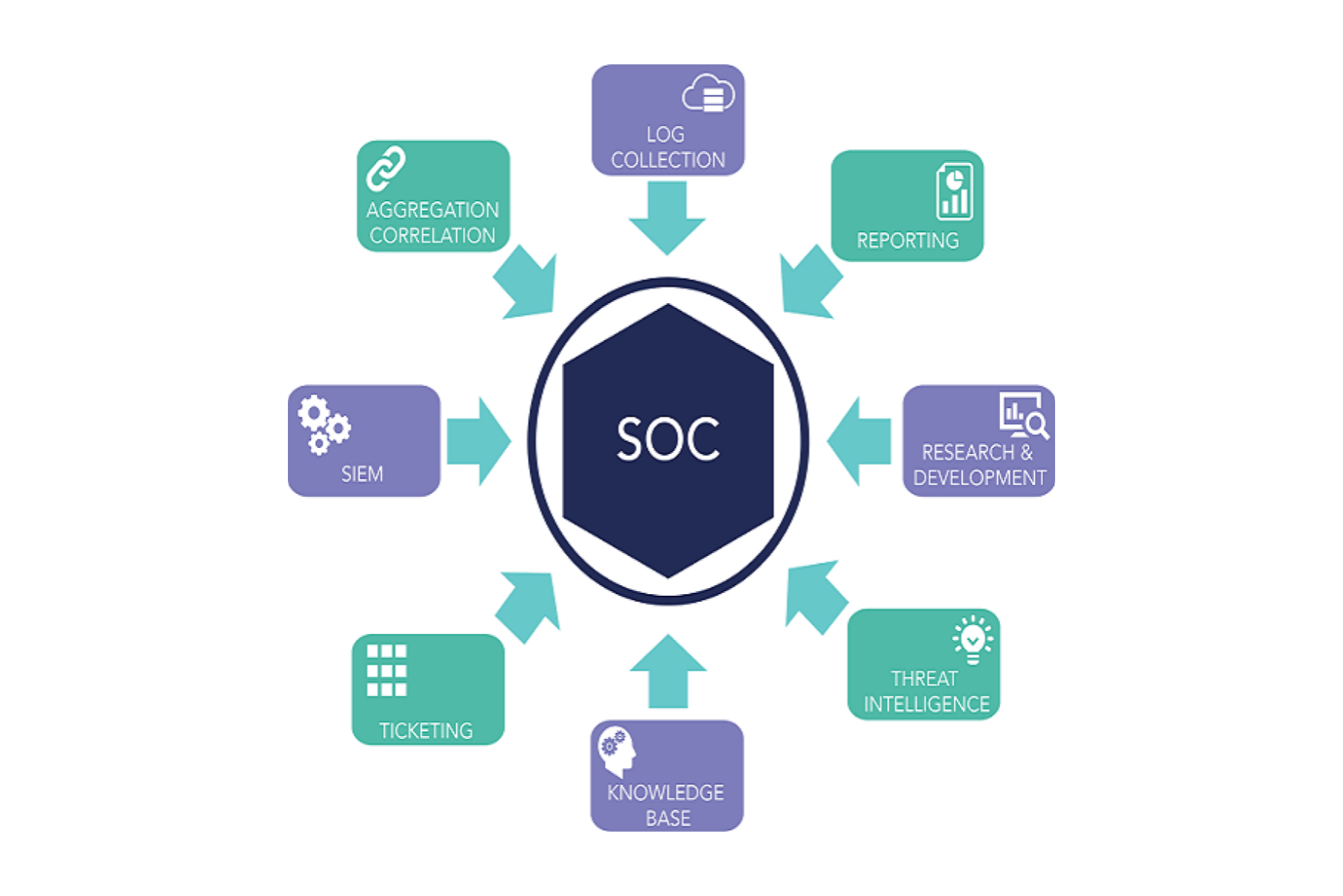
ADVANTAGES OF THE SOC SERVICE
Actionable Alerts & Noise Cancellation ¤ The customer's network is monitored 24x7 by dedicated appointed SOC analysts. ¤ Each detected alert is triaged and custom incident report tickets are created manually. ¤ Noise is suppressed & only true positives are escalated - customers don't have to deal with overwhelming alerts and false positives. 24x7 access to SOC and customer data ¤ The customer has full access to search through the ingested SIEM logging data. ¤ The customer has access to the SOC ticket management portal. Real-time incident alerts and 24x7 SOC triage. ¤ SOC analysts are available to respond to incident containment calls (at no additional cost). 24x7 access to knowledgeable named SOC analysts.

SMART CITY
The smart city is a new concept of urban development. The aim is to improve the quality of life of city dwellers by making the city more adaptive and efficient, using new technologies that rely on an ecosystem of objects and services.
SCADA
¤ Protect industrial networks such as automotive, oil & gas, water, power/grid, manufacturing, and others from cyber threats, malicious insiders, and human error. ¤ Maximize visibility, security and control of your operational environments for SCADA systems, PLCs, DCS, IEDs, HMIs and more. ¤ Get all the security tools and reports for your IT and OT engineers, providing unparalleled visibility into converged IT/OT segments and ICS networks in a single window.

IT EXAM
A full evaluation of your information security and IT policies, procedures and controls will determine the adequacy of your security and risk management efforts. Our IT exam identifies areas where you’re most at risk and provides a detailed review of your environment to confirm compliance with industry regulations and guidelines. Recommended actions are provided as a road map to ensure your institution has a well-secured and compliant IT environment

WHAT SPSM/MSSPS AND END CUSTOMERS GET
¤ 24x7 detection, analysis and triage of threats in a multi-tenant environment. ¤ Custom reports without white label. ¤ Weekly/monthly SOC reports. ¤ Recurring SOC governance calls. ¤ Access to customer data. ¤ Over 750 custom security rules. ¤ Access to the SOC ticket management portal. ¤ Automation and incident response. ¤ Custom SOC Escalations. ¤ ALS GOLD of 30 minutes. ¤ Retention of logs from 90 days to 1 year. ¤ Assigned named SOC analysts. ¤ Local number dedicated to SOC 1800.

ADVANTAGES OF THE SOC SERVICE
Actionable Alerts & Noise Cancellation ¤ The customer's network is monitored 24x7 by dedicated appointed SOC analysts. ¤ Each detected alert is triaged and custom incident report tickets are created manually. ¤ Noise is suppressed & only true positives are escalated - customers don't have to deal with overwhelming alerts and false positives. 24x7 access to SOC and customer data ¤ The customer has full access to search through the ingested SIEM logging data. ¤ The customer has access to the SOC ticket management portal. Real-time incident alerts and 24x7 SOC triage. ¤ SOC analysts are available to respond to incident containment calls (at no additional cost). 24x7 access to knowledgeable named SOC analysts.

SMART CITY
The smart city is a new concept of urban development. The aim is to improve the quality of life of city dwellers by making the city more adaptive and efficient, using new technologies that rely on an ecosystem of objects and services.

SCADA
¤ Protect industrial networks such as automotive, oil & gas, water, power/grid, manufacturing, and others from cyber threats, malicious insiders, and human error. ¤ Maximize visibility, security and control of your operational environments for SCADA systems, PLCs, DCS, IEDs, HMIs and more. ¤ Get all the security tools and reports for your IT and OT engineers, providing unparalleled visibility into converged IT/OT segments and ICS networks in a single window.
Certified Professionals









